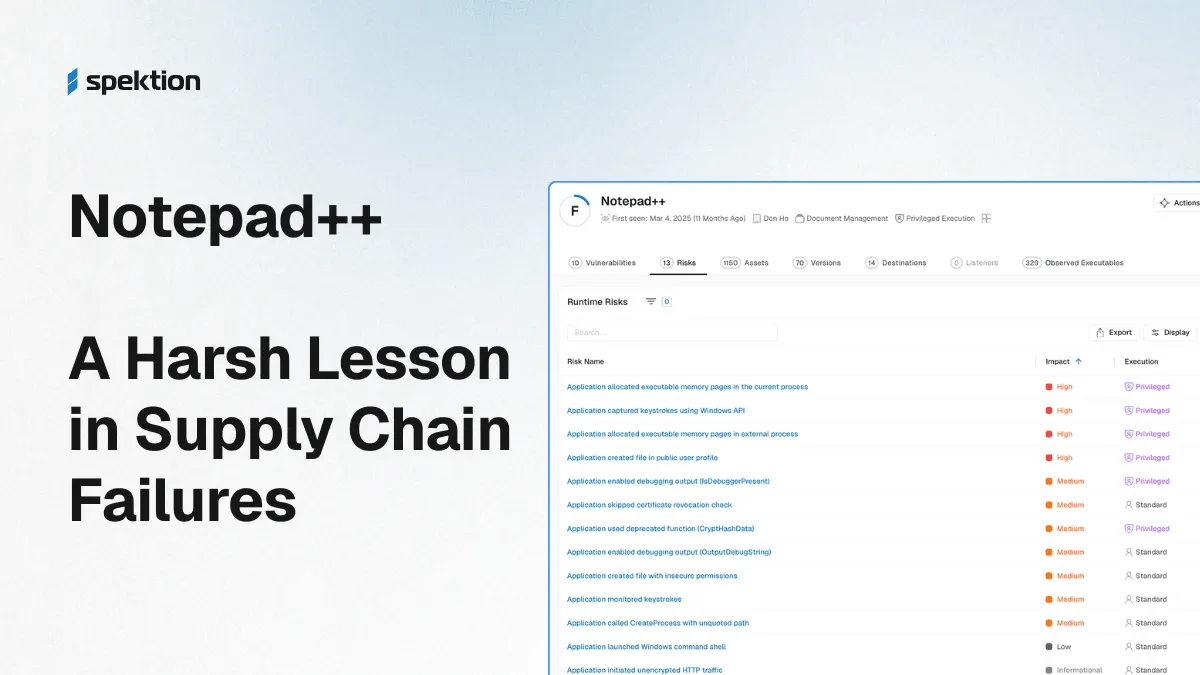
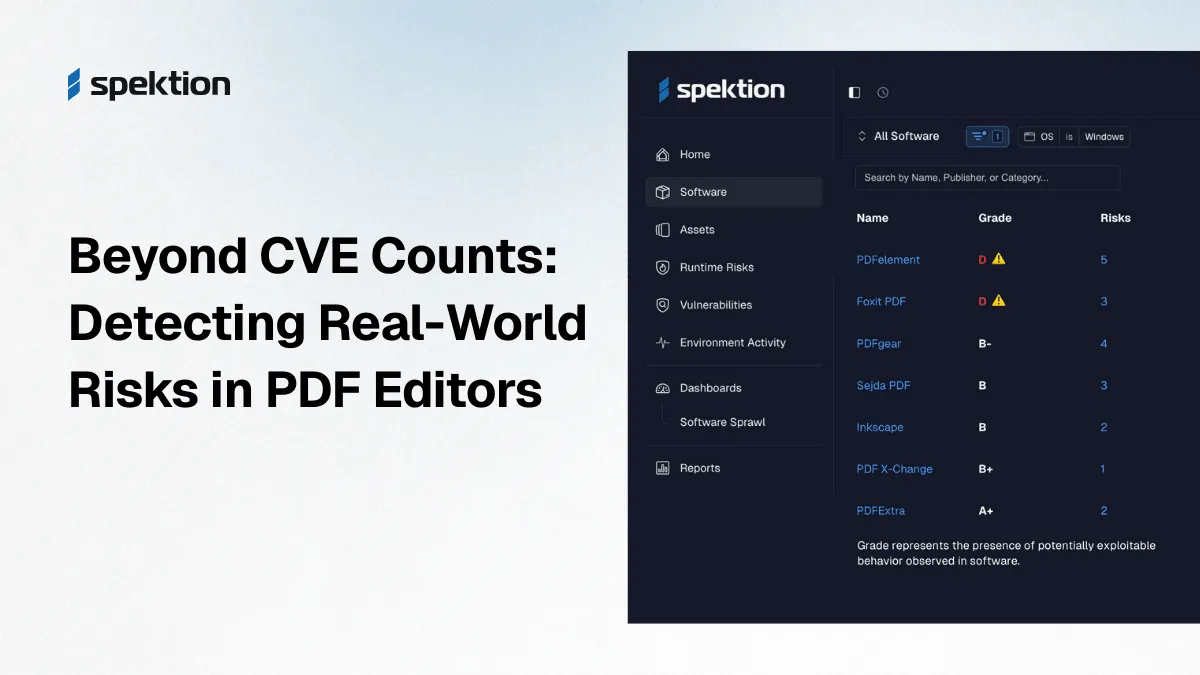
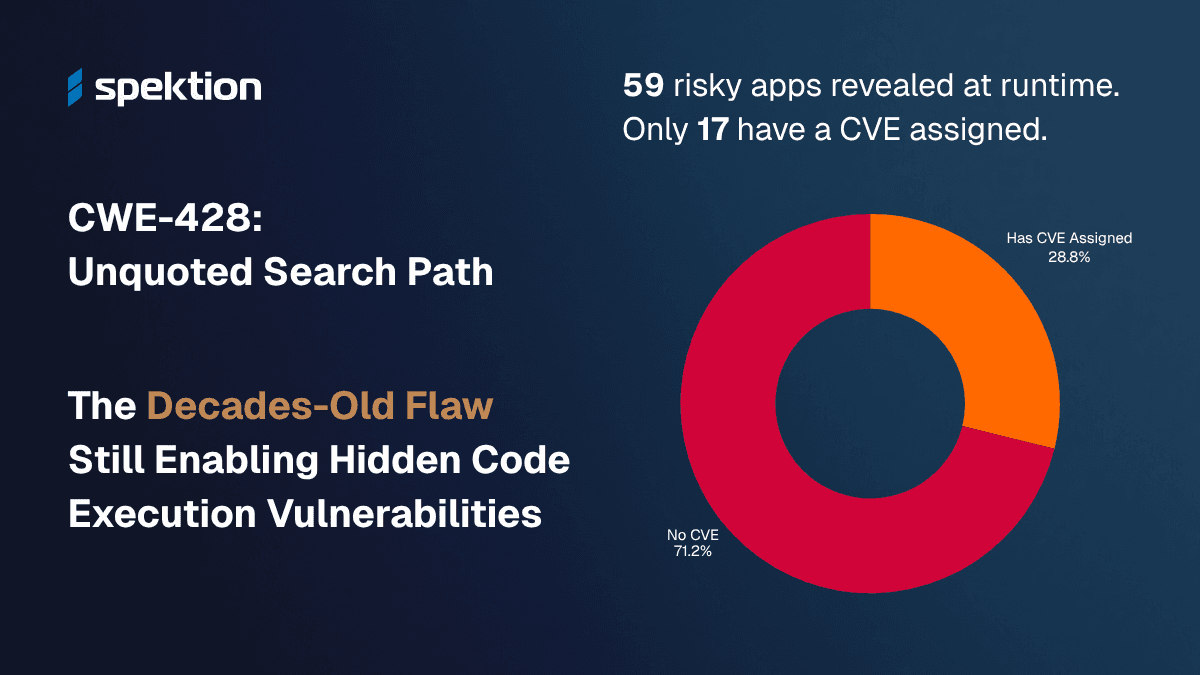
Transform Your Vulnerability Management Program. Together.
We are committed to helping enterprises take a more proactive, efficient, and effective approach to software vulnerability management. By providing our customers with unprecedented visibility into software behavior, we can enable them to dramatically increase them maximize their risk reduction and increase their return on their vulnerability management investment.