AI-Powered Citizen Development Security Risks And How To Address Them
AI copilots and citizen development are creating untracked software inside enterprises. Learn how Spektion exposes hidden risks at runtime.
Published on
AI copilots and low-code/no-code tools are fueling a new wave of citizen development. Anyone in the business, not only developers, can build and deploy software to solve problems and move faster.
The risk isn’t just in the cloud; it’s on workstations and servers in your network. Citizen developers are generating code that runs inside your environment without AppSec, including executables, scripts, and automations.
At Spektion, we see this trend across customer environments: internally built software ranks among the top five types of installed applications on all endpoints, and its footprint continues to grow.
AI-generated, locally installed tools are invisible to scanners, absent from CVE databases, and rarely reviewed before execution. That creates a dangerous visibility gap.
Gartner forecasts that by 2026, developers outside of IT departments will make up at least 80% of low-code platform users (up from 60% in 2021). This surge in development means software creation is accelerating, likely beyond traditional security oversight.
From our work helping enterprises identify and assess all installed software at runtime—commercial, internal, or AI-generated—one pattern is clear: the rise of AI-assisted citizen development is creating a new frontier in vulnerability management.
Here’s why:
- Exploitable vulnerabilities in internally developed apps are never assigned a CVE.
- Without runtime visibility, these exposures remain invisible to traditional vulnerability management programs.
- In many cases, companies only learn about citizen-developed apps and their risks after they’ve been exploited.
Don’t wait for an attacker or audit to reveal what’s already running in your environment. Learn how Spektion’s Runtime Vulnerability Management brings hidden risks into view.
This article draws on Spektion’s customer experiences to provide a brief overview of how to recognize and address the emerging challenges of citizen-developed applications and resources.
The Security Impact of AI-Powered Citizen Development (And “Just-In-Time Code”)
When organizations first run Spektion, they’re often surprised by what its real-time software inventory reveals. Our platform surfaces everything that’s executing on endpoints and servers, and almost always, that list includes internally built or citizen-developed tools the organization didn’t know existed.
However, once visible, many of these applications show critical vulnerabilities: exploitable memory mismanagement, overprivileged execution, and injectable conditions that attackers can weaponize.
These findings align with OWASP’s Low-Code/No-Code Top 10, which identifies injection flaws, insecure data handling, and excessive privilege misuse as critical risks in citizen-developed tools. Given that AI copilots are driving faster, more frequent code creation, it is reasonable to expect that these same vulnerabilities will appear more often in enterprise environments.
One recent study found AI-generated code introduced vulnerabilities in 45% of test cases, with insecure implementations chosen almost half the time, and 30% of developers say they don’t fully trust AI-written output.
AI isn’t eliminating insecure code; it’s creating more of it faster.
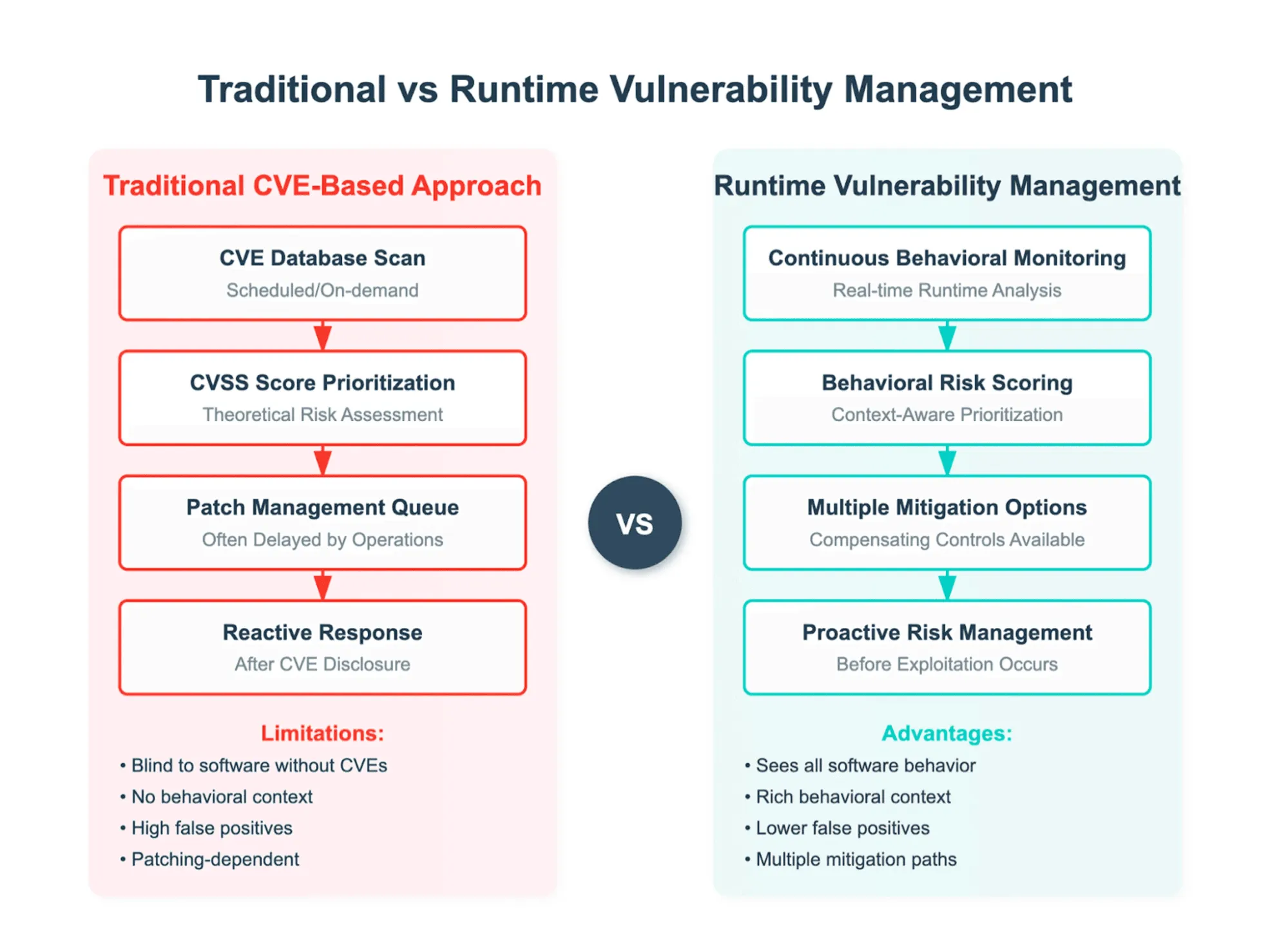
Why Traditional Vulnerability Management Falls Short
Traditional vulnerability management relies on two pillars: published CVE identifiers and scheduled scans. Both fail in the world of AI-driven citizen development:
- No CVEs for internal tools. Apps built for internal use never appear in public vulnerability databases because they aren’t widely distributed and often go unnoticed. Without an identifier, scanners simply don’t register them and the exploitable vulnerabilities they may contain. In practice, this means there could be hundreds of vulnerable scripts, macros, and internal web apps inside your network that no scanner ever examines or scores for risk.
- No visibility into unknown apps. Many homegrown apps are never included in asset registers or vulnerability programs, remaining invisible to traditional software discovery tools and not subject to manual analysis by security teams.
- No shift-left option. Citizen development is just-in-time coding that, by its nature, has no SDLC or AppSec, so there is no repository of pre-release vulnerability data for security teams to reference.
That means vulnerabilities in citizen-developed apps are often discovered first by attackers or (if you’re lucky) by red teams simulating them.
Just-In-Time Vulnerability Management At Runtime
The only way to address the challenge of citizen-developed apps is to move vulnerability detection and risk scoring into runtime.
Spektion’s Runtime Vulnerability Management (RVM) continuously analyzes how software behaves during operation, detecting new scripts and executables in real-time, regardless of who wrote them and whether they’re on your asset register or have a CVE.
Learn more about what Runtime Vulnerability Management is
Spektion customers use Runtime Vulnerability Management technology to:
- Continuously identify and highlight risks in all citizen-developed software assets, along with all installed software, in their environment in real time.
- Score exploitability with context (asset criticality, exposure, blast radius) and allow-list safe, useful resources.
- Justify the removal of dangerous assets from the modification of existing environment access policies.
- Automatically identify and block exploit paths of resources that can’t be removed.
- Integrate findings into VM, SIEM, and ITSM systems to establish a detection and response workflow tailored to their environment.
With runtime visibility, security teams gain a live, defensible picture of what’s really installed and risky and the leverage to act before attackers do.
Discover and De-Risk Your Citizen-Developed Resources
Citizen development is here to stay. Today, 81% of companies view low‑code as strategically important, and 31% have made it central to their software strategy.
In many organizations, leadership is pushing to democratize development and expand API access to accelerate innovation. You don’t have to stand in the way of this trend to respond safely.
Real-time, behaviour-based governance enables IT and security teams to identify precisely where risks are emerging in their environment and respond with defensible evidence.
Spektion helps you discover and manage the dozens to thousands of internally developed assets installed in your environment with real-time runtime insights so that you can have consistent visibility and controls across your entire attack surface.
Want to see what’s running in your environment? Book a demo.