What Is Runtime Vulnerability Management (RVM)?
Learn what runtime vulnerability management (RVM) means, why it's the next evolution of vulnerability management, and how it can surface risks from supply chain software to shadow IT applications.

Published on
Runtime vulnerability management (RVM) is a new technology that assesses live, real-world exploit risk based on how software, including third-party, open-source, and internal applications, behaves while running.
Runtime vulnerability management (RVM) solutions, such as Spektion, surface exploitable risks without relying on CVEs.
An RVM tool passively monitors software at the lowest level of observable activity - runtime processes.
Poor risk prioritization. CVSS scores are lagging risk indicators. They are based on publicly sourced and reactive data. They also don’t reflect real-world risk in your specific IT environment at a given point in time. A high-severity CVE might be harmless in your environment, while a lower-severity one could be used in a dangerous exploit chain.
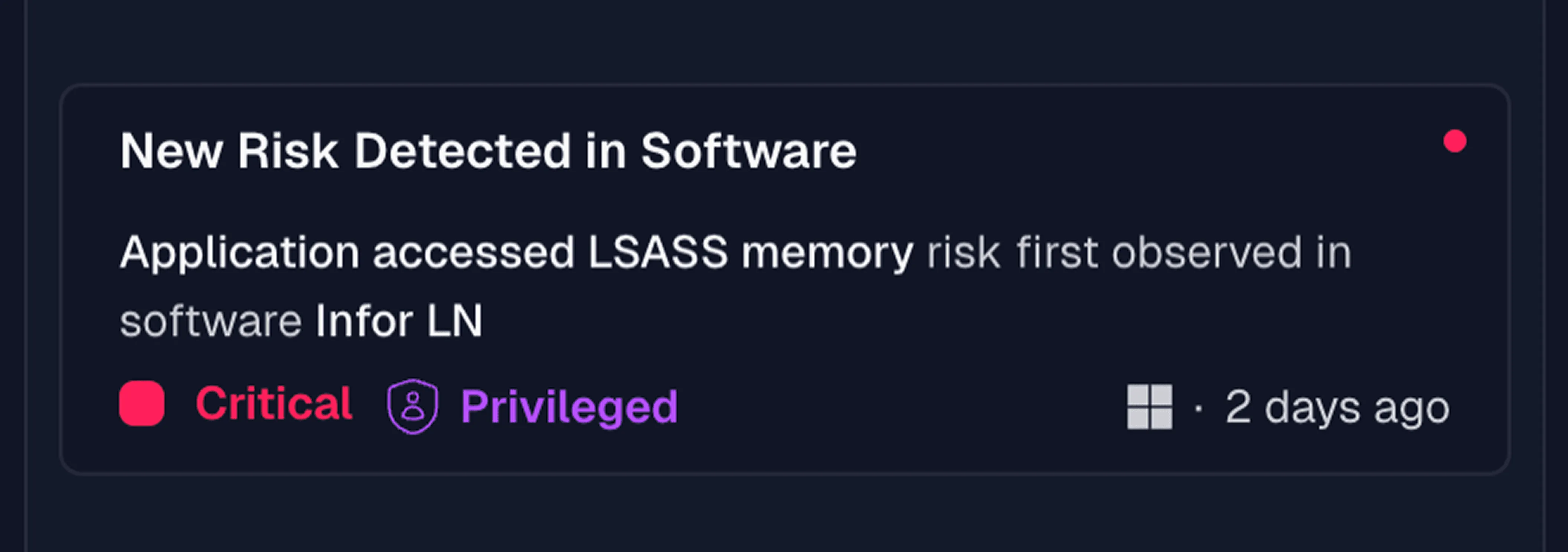
Why start vulnerability management at runtime?
Runtime is the operational environment created when an application is running. It’s also the best possible source of truth for efficient and safe vulnerability management.
By monitoring runtime, RVM depicts the risk of software based on how it runs in your environment, sparing you from worrying about theoretical risks that never manifest.
Runtime monitoring detects risky actions, misconfigurations, or privilege escalations that traditional tools may never flag.
Insecure processes in runtime interactions between software, code, and hardware are what create the exploitation paths that eventually become CVEs or form parts of dangerous exploitation chains. An exploitable runtime process, such as a remotely accessible named pipe that is writeable without authentication, can turn a software application with few or no severe CVEs into a highly exploitable source of risk.
Start vulnerability management by monitoring these runtime processes (instead of waiting for the results of an exploitable process to be flagged within a CVE report), and you’ll get a focused and realistic picture of risk in your environment, including live data enriched with CVSS scoring.
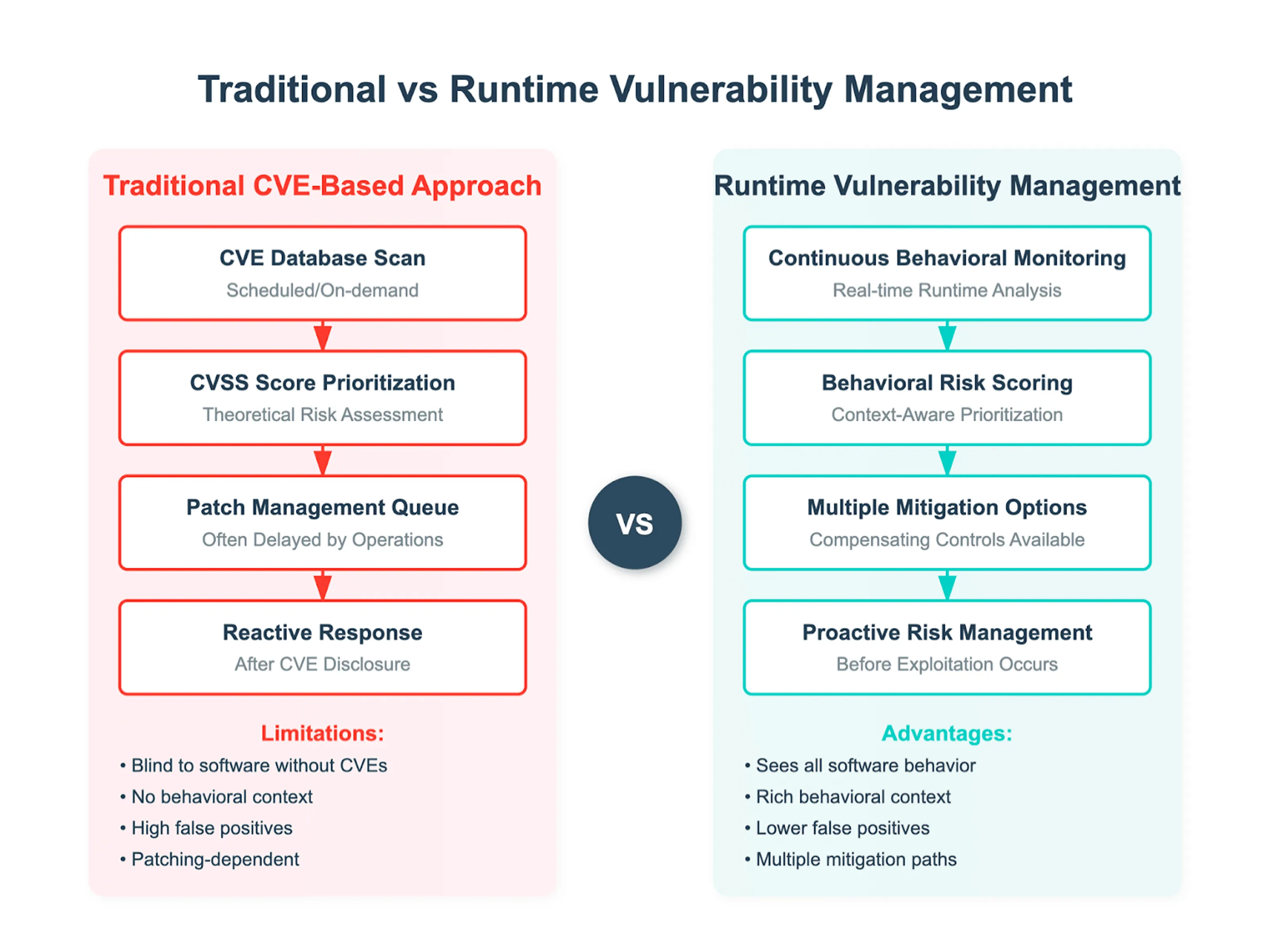
By building your understanding of risk from what happens at runtime, you can prioritize real risks as your core remediation priority rather than theoretical CVEs.
RVM also shows vulnerability management teams dangerous risks in software applications they would otherwise never get to see:
- Risks from your software supply chain and proof-of-concept (POC) software.
- Exploitable software processes without a CVE (e.g., memory pages with both writable and executable permissions) and zero-day risks.
- Shadow IT applications not listed in your asset register.
CVEs still play a role. However, with RVM, their purpose is to enrich live data from the runtime environment rather than act as the starting point for vulnerability management.
RVM Solves CVE-Centric Vulnerability Management Limitations
CVEs help teams theoretically understand and communicate known software vulnerabilities, but they do not provide a complete picture of real-world risk.
That’s why a vulnerability management program based only on CVEs has some major limitations:
- Blind spots beyond CVEs. Traditional tools miss risks in proprietary, niche, or forked open-source software without CVEs.
- Poor risk prioritization. CVSS scores are lagging risk indicators. They are based on publicly sourced and reactive data. They also don’t reflect real-world risk in your specific IT environment at a given point in time. A high-severity CVE might be harmless in your environment, while a lower-severity one could be used in a dangerous exploit chain.
- Reliance on patching. Patching as the sole or primary solution to managing software vulnerability risk has proven ineffective, as evidenced by the fact that third-party software is a leading cause of breaches.
- CVE overload. Vulnerability teams struggle to prioritize critical and high-severity vulnerabilities, often due to limited IT patching capacity, which creates a negative dynamic between security and IT.
- Lack of visibility. No risk insights into software without CVEs. Inversely, SBOMs often generate so many CVEs (most of which don’t matter) that teams can’t see the important ones.
- Lack of staff. Teams don’t have enough analysts and offensive security/red team staff to thoroughly investigate software security risks.
Hundreds of thousands of CVEs live in a typical environment. Most are not dangerous, but some are very dangerous. Other vulnerabilities, including those that you cannot see with a vulnerability scan of your environment, can create extreme risk.
- Many high-profile attacks involve zero days, and zero days are increasingly targeting corporate systems. According to Google’s latest threat intelligence report, 44% of zero-day exploits in 2024 targeted software in corporate systems, up from 37% the previous year.
- Only a small percentage of CVEs (even severe ones) are ever exploited, but the ones that are exploited are compromised rapidly. 159 CVEs were exploited in Q1 2025. Of these, 28.3% were exploited within 24 hours of disclosure.
Runtime vulnerability management is the answer to these challenges.
It helps security teams take a shift-left approach to software that is already running in their environment by letting them start upstream of CVEs.
Why Organizations Choose Runtime Vulnerability Management
Vulnerability management teams use RVM as a source of truth for real-time risk-based vulnerability management.
- Spektion customers, such as NielsenIQ, Granicus, and Juul Labs, use RVM to evolve their vulnerability management programs. A continuous, real-time view of risk means that they can tackle sprawling IT environments, including risks from internal AI-generated tools and third-party software that were never developed securely.
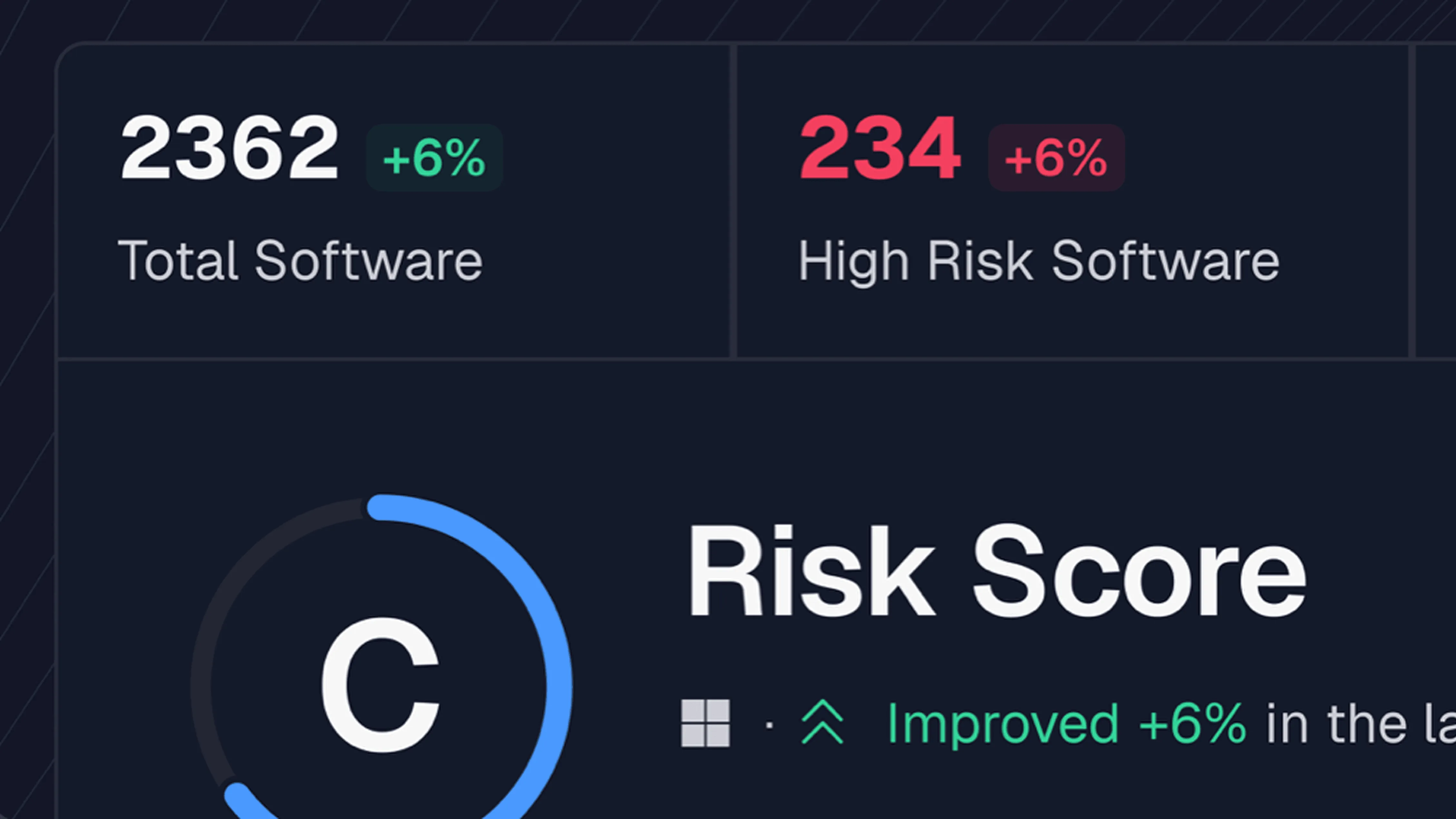
By basing vulnerability management off of runtime risks, you can immediately see and prioritize vulnerabilities based on risks, not just CVSS scores.
The core advantage of RVM is the ability to proactively manage your vulnerability risk
With RVM, you can prioritize fixing the small percentage of vulnerabilities that could actually be used to compromise your systems, anticipate and head off real-world supply chain risks, and effectively get the benefit of continuous offensive security testing at scale.
RVM shows provable risk in real time and helps security teams do the following:
Mitigate vulnerabilities
When you enhance your vulnerability management program with RVM, you can continuously monitor real software behavior in your environment and get a much richer understanding of risk.
Small vulnerability management teams can use RVM to get clear, behavior-based prioritization that doesn’t require deep manual analysis of every potential risk.
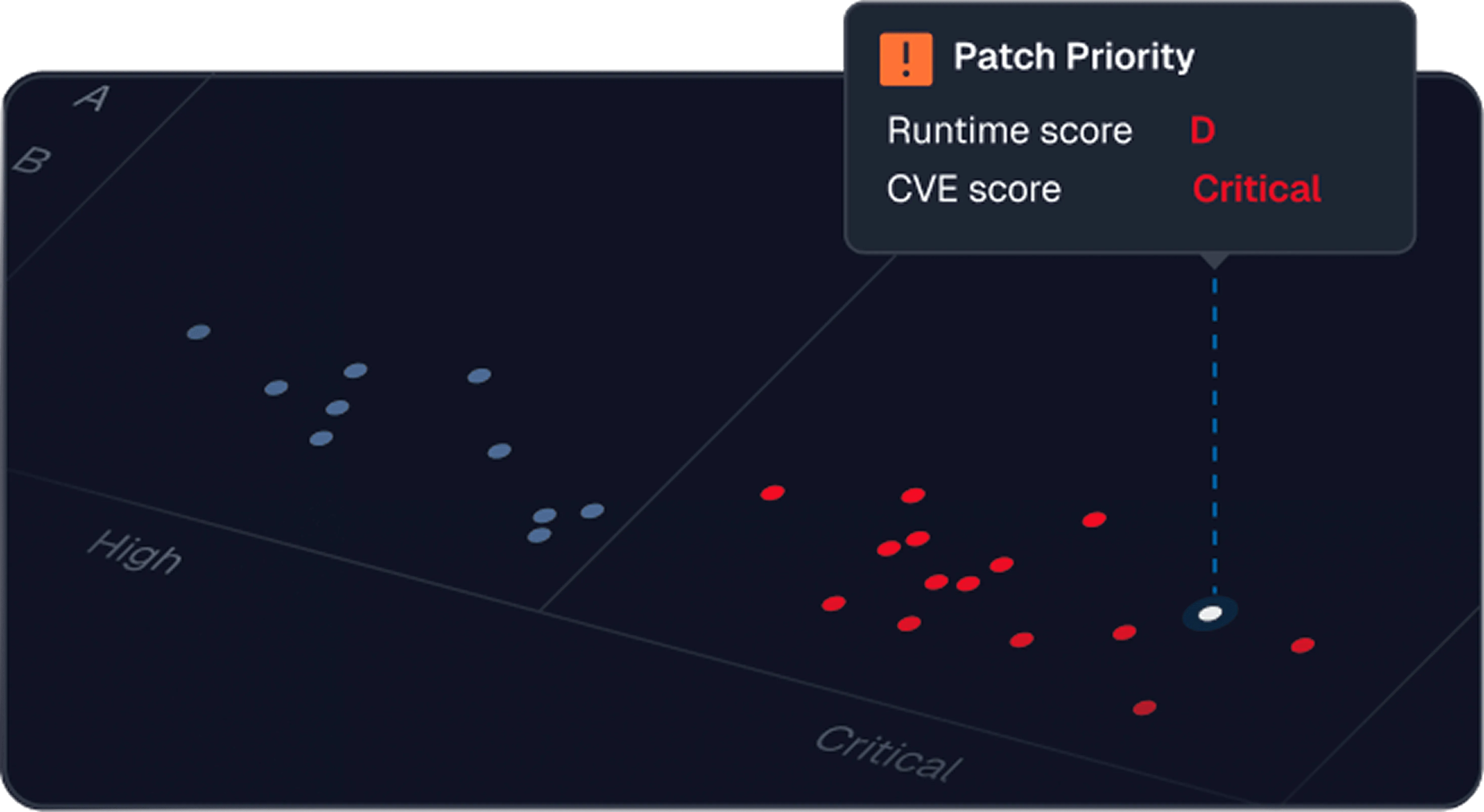
The immediate outcome of doing so is being able to detect risky behaviors before they result in a CVE and show the contextual risk (and patch priority) of vulnerabilities that do not have a CVE.
This means that security teams can:
- Flag security issues the moment they emerge, not after public disclosure.
- Quantify risk from software sprawl across their environment.
- Identify behavior that suggests supply chain or vendor compromise.
To see how RVM works in your environment, contact us for a free Spektion demo.
Uncover pre-purchase software risks
Third-party software is consistently a top cause of breaches in annual surveys, such as the Verizon Data Breach Incident Report.
A core reason why is that security considerations often come too late in the procurement process.
In many cases, security teams lack the time or specialized skills needed to thoroughly test every application to ensure it meets security standards. RVM addresses this challenge by enabling risk assessments early before the software is rolled out.
With RVM tools like Spektion, security teams can monitor software during proof-of-concept testing while functionality is being evaluated. This approach is especially valuable in regulated environments where thorough security assessment is mandatory.
RVM makes software assessment truly scalable by enabling security evaluation concurrent with functional testing by non-security teams, making security assessment a seamless part of the procurement process rather than a bottleneck.
Reduce zero-day risks
Zero-day exploits do not have CVEs, but you can still predict and prevent them with RVM.
Teams can use an RVM solution, such as Spektion, to leverage their existing security controls and manage vulnerability risk at the runtime level.
This means that rather than waiting for a CVE to be disclosed and entering a race with attackers to see if they can patch or isolate a risk before it is exploited, security teams can preemptively secure at-risk assets.
Reveal shadow software risks
The risk shadow IT creates is immense and growing as AI-generated “vibe-coded” applications proliferate.
- Organizations already manage an average of 668 applications, with over half (54%) classified as shadow IT.
- As many as 49% of all cyber attacks involve shadow IT assets.
- 72% of IT leaders flagged “shadow AI” as a major risk in 2024. With noncorporate leaders encouraging employees to code their own solutions, this risk is set to soar. “vibe coding” searches are up 6700% in the last 3 months.
Scanning your environment for shadow IT software will likely highlight hundreds of shadow IT applications. It also poses a tricky question: Which ones do you focus on first?
The best way to answer that is through a risk-based approach. Rather than treating all shadow IT equally, evaluate how each application behaves at runtime. Some may operate securely and pose minimal risk, but some may have inherent runtime flaws that attackers could exploit.
Runtime Vulnerability Management vs CVE-Based Vulnerability Management
Runtime vulnerability management is a natural evolution of CVE vulnerability management technology.
This is why it makes sense to compare these two generations of vulnerability management tools as we’ve done in the table below:
| Feature | Runtime Vulnerability Management (RVM) | CVE-based vulnerability management tools |
|---|---|---|
| Focus | Behavior of software during runtime. | Scan software for known vulnerabilities (e.g., CVEs). |
| Timing | Detects risk in real time, as software runs. | Reacts after vulnerability disclosures and from scheduled scans. |
| CVE Dependence | Not reliant on CVE coverage. Enriches known CVEs with context, but also flags risks without CVEs. | Depends on CVE databases. |
| Context Awareness | High. Evaluates risk based on runtime context and system state. | Low. Flags based on metadata or version info. |
| Coverage | Captures both known and unknown risks. | Limited to known CVEs and configurations. |
| False Positives | Lower based on observed activity. | High. Often lack real execution context. |
| Detection Scope | Include privilege misuse, misconfigurations, and runtime anomalies in known and unknown software applications. | Focus on patching outdated or vulnerable known software |
How Does Runtime Vulnerability Management Work?
An RVM platform builds a baseline of normal runtime behavior and then flags deviations.
These deviations might include:
- An AI-generated tool suddenly performing privileged operations.
- A trusted application accessing sensitive memory regions unexpectedly.
- Software establishing network connections outside normal patterns.
- Applications requesting elevated privileges beyond their baseline behavior.
- Processes exhibiting characteristics consistent with exploitation attempts.
By combining behavioral signals with known vulnerability data, runtime analysis can see this behavior in real time and give you a direct view into what’s actually risky in your environment, not just what’s theoretically vulnerable.
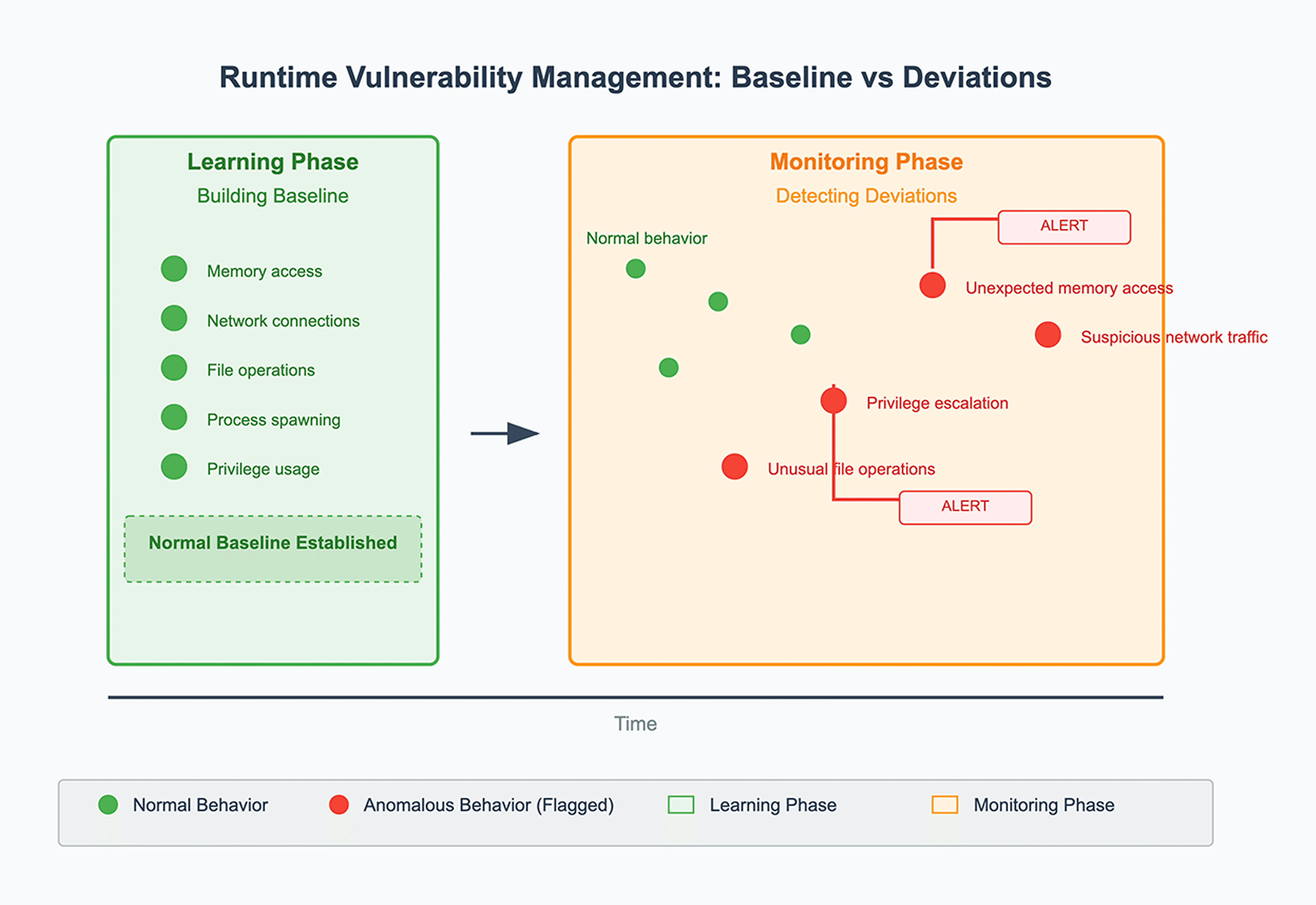
For more information on runtime vulnerability in action, learn more about how Spektion’s runtime vulnerability management tool can flag otherwise unseen risks created by:
Using Runtime Vulnerability Management
RVM uses a lightweight agent deployed on systems across your environment to monitor installed software. With Spektion, it can be managed through an easy-to-use dashboard.
This agent gives IT and security teams immediate visibility into the real-world impact of software the moment it begins to behave suspiciously. An installed agent is necessary to get real visibility into software behavior.
Spektion’s RVM deployment process is designed for rapid implementation.
Teams begin seeing value within days without requiring dedicated engineering resources for ongoing management. The behavioral analysis insights from a sample of systems can be extrapolated to understand the organization’s risk posture across all systems.
Getting Started with Runtime Vulnerability Management
Organizations typically start their RVM journey with a proof-of-concept deployment of Spektion to evaluate the behavioral insights and risk reduction potential it can deliver in their specific environment.
The implementation process generally follows these steps:
- Initial consultation and demo to understand your specific vulnerability management challenges.
- In-depth demonstration with your broader security and IT teams.
- 2-4 week proof-of-concept deployment to evaluate real-world effectiveness.
- Procurement and full deployment based on demonstrated value.
The goal is to transform your vulnerability management program from reactive CVE chasing to proactive risk management based on actual software behavior in your environment.
Ready to see how runtime vulnerability management can transform your security posture?
Contact us for a demonstration of RVM in action within your environment.
Runtime Vulnerability Management FAQs
The following are some of the most frequently asked questions we receive about runtime vulnerability management.
Does runtime vulnerability management replace CVEs?
No. RVM doesn’t aim to totally replace the CVE-based understanding of software risks. Instead, it significantly improves CVE scores with behavioral data. Modern RVM solutions, such as Spektion, include CVEs as an enrichment to the runtime visibility they provide, creating a more comprehensive picture of your actual risk landscape.
What’s the difference between runtime vulnerability management vs AppSec?
Runtime vulnerability management focuses on the behavior of software while it’s running to identify risk regardless of CVE coverage. On the other hand, application security focuses on code, configuration, and known issues before or during deployment to prevent vulnerabilities from reaching production.
Critically, RVM can assess risks in software you don’t own, including third-party applications and supply chain software, while traditional AppSec tools are limited to code you control.
How is runtime vulnerability management different from RASP, EDR, or DAST/SAST/SCA tools?
Runtime vulnerability management vs RASP: While RASP focuses on individual web applications, RVM delivers broader visibility across your entire environment. RASP must be embedded into each application, making it hard to scale. In contrast, RVM monitors all software at runtime, providing comprehensive, system-wide risk insights.
Runtime vulnerability management vs EDR: RVM complements EDR by providing visibility “left” of your EDR deployment. While EDRs deliver real-time visibility into attack activity after exploitation attempts, RVM offers real-time visibility into software exploitability, enabling the prevention of exploitation in the first place.
Runtime vulnerability vs DAST/SAST/SCA: DAST/SAST/SCA tools focus on code analysis and testing during development phases. RVM monitors the actual runtime behavior of deployed software, including third-party and legacy applications you cannot test with traditional AppSec tools.
What problems does runtime vulnerability management solve that we can’t solve otherwise?
RVM specifically addresses the following:
CVE overload: Instead of having to deal with thousands of theoretical vulnerabilities, teams can focus on the behavioral risks that actually matter in their environment.
Limited visibility: Gain risk insights into software without CVEs while filtering SBOMs to highlight truly important risks among the noise.
Resource constraints: Increase the effectiveness of small vulnerability management teams by providing clear, behavior-based prioritization that doesn’t require deep manual analysis of every potential risk.
← Back to all use cases