How to Assess Third-Party Software Security
A practical guide to evaluating third-party software risk before purchase, after deployment, and continuously at runtime.

Published on
Security pros, IT teams, and sysadmins all wrestle with the same question: “How do I actually know if this software is secure?”
It sounds straightforward, but in practice, it’s one of the hardest problems to solve.
New tools arrive almost daily, users request exceptions, and business leaders want productivity gains without delay. Meanwhile, attackers increasingly target third-party and commercial software as a way into enterprise environments. In fact, third-party software was the #2 cause of breaches in the 2025 Verizon DBIR.
Despite the risk, most organizations still rely on paperwork, vendor assurances, or hope when deciding what to install. That gap between what we need to know and what we actually see is why evaluating software security remains such a persistent pain point.
Understanding the Status Quo in Third-Party Software Vetting
Here’s what usually happens when organizations try to vet new software:
- They send vendors a security questionnaire or ask for SOC 2 / ISO documentation.
- They sometimes spin up a sandbox or test VM, maybe run some antivirus or EDR checks.
- They do a pilot deployment on a few machines.
- They rely on peer reviews and brand reputation (“if BigBankCo uses it, it must be fine”).
- They may do a security architecture review based on vendor documentation and attestations.
None of those are bad steps. But let’s be honest: they’re all indirect. They don’t actually show how the software behaves when it’s running on your systems in your environment.
When teams do want to deep dive to understand security risk, it’s a labor-intensive exercise that doesn’t scale to address the volume of software already in the organization and the velocity of new software coming in, both through governed request processes and unauthorized installs or local admin privileges.
Understanding how software behaves when it’s running in your environment is the missing piece for assessing third-party software risk.
Think about it: a SOC 2 report tells you the vendor’s processes, not whether their code opens a risky network socket on install. A sandbox shows you a snapshot, not how the software behaves a week later.
Even limited pilots rarely show the full picture of software risk.
They only capture a narrow slice of environments and integrations, and mostly reflect behavior at install or in a short trial window. What they miss are the things that emerge over time, such as silent updates, version drift, patch cycles, or hidden components that don’t surface until the software is broader in production.
That’s why so many practitioners remain uneasy: they want certainty. What they get instead is paperwork, guesswork, and hope.
Prove Third-Party Software Security Controls
Spektion allows you to assess third-party software security based on real data from your environment.
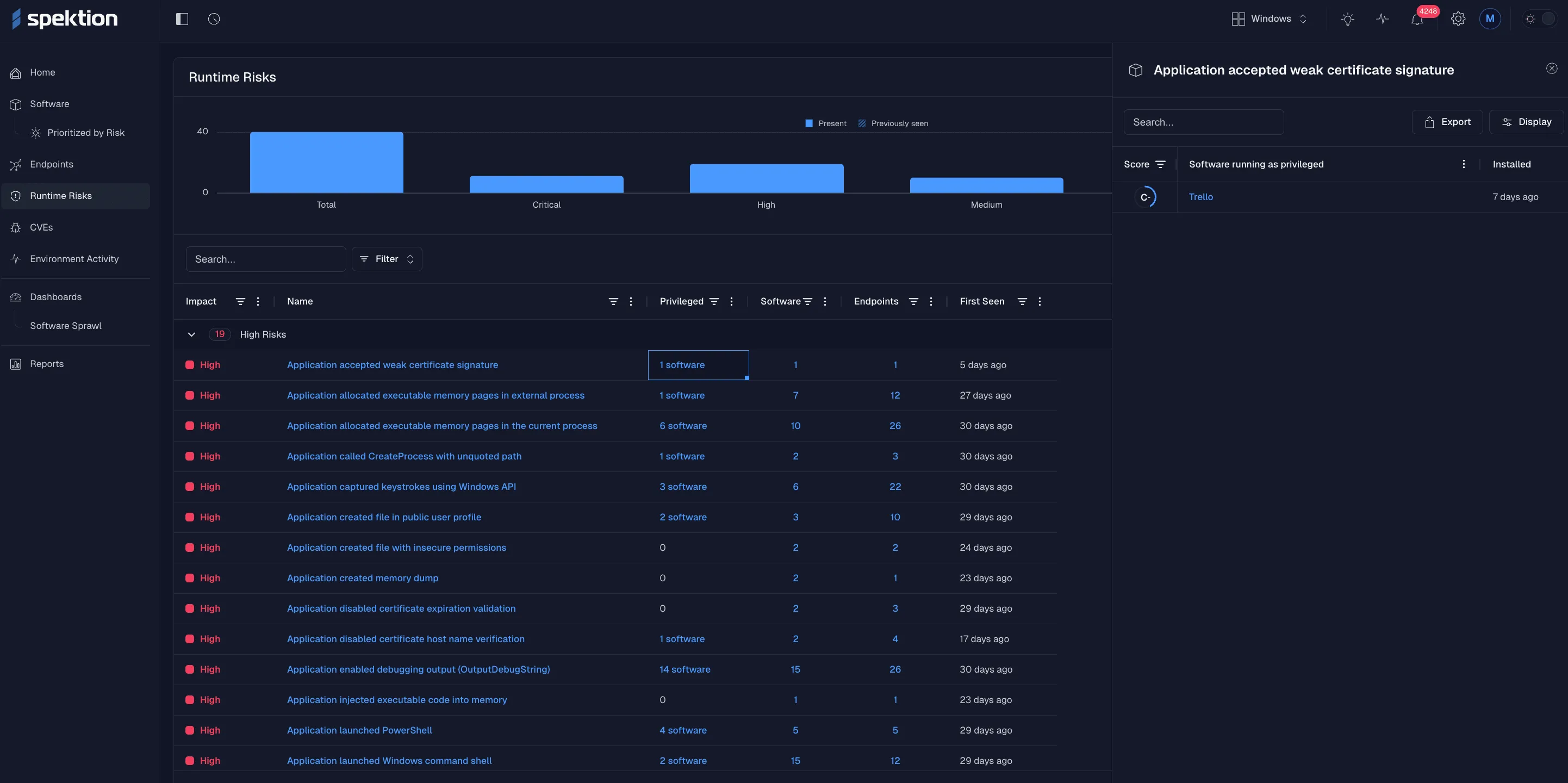
Spektion’s runtime risks dashboard. This view is after a click into the highlighted cell to see more about that risk in the right pane.
Instead of treating evaluation as a paper exercise, you can actually watch the software run.
Whether you’re installing the vendor’s product on a handful of machines to start, or taking the leap with a full deployment, Spektion sees third-party software behavior in real time at runtime, including:
- What processes it spawns.
- What network calls it makes.
- What privileges it uses.
- Whether it tries to access sensitive memory or files.
- Whether it calls functions in a way that is susceptible to injection.
That’s not theory; it’s evidence. And runtime evidence doesn’t just create more noise. Spektion translates what it sees into a unified risk score (0–100 / F–A), allowing teams to quickly distinguish between minor issues and the exposures that truly matter.
If you evaluate software first, you can use Spektion to make a data-driven decision before rolling it out widely.
If you buy first or acquire through M&A activity, you can use Spektion in production to know what’s running in the newly acquired entity and assess software before it comes inside your corporate network.
Either way, you finally get visibility into what your software is actually doing, not just what the vendor says it does.
And with visibility comes accountability. Cloud companies have long promoted a “shared responsibility model” for security. Spektion brings that same concept to third-party software. As the customer of third-party software, you gain evidence to hold vendors accountable: show them where their product is insecure and push them to fix it.
It also reinforces what many security leaders already advise: prioritize resilience over features, find risks before adversaries do, and demand stronger partnerships with vendors. Spektion provides you with the data to make those expectations a reality.
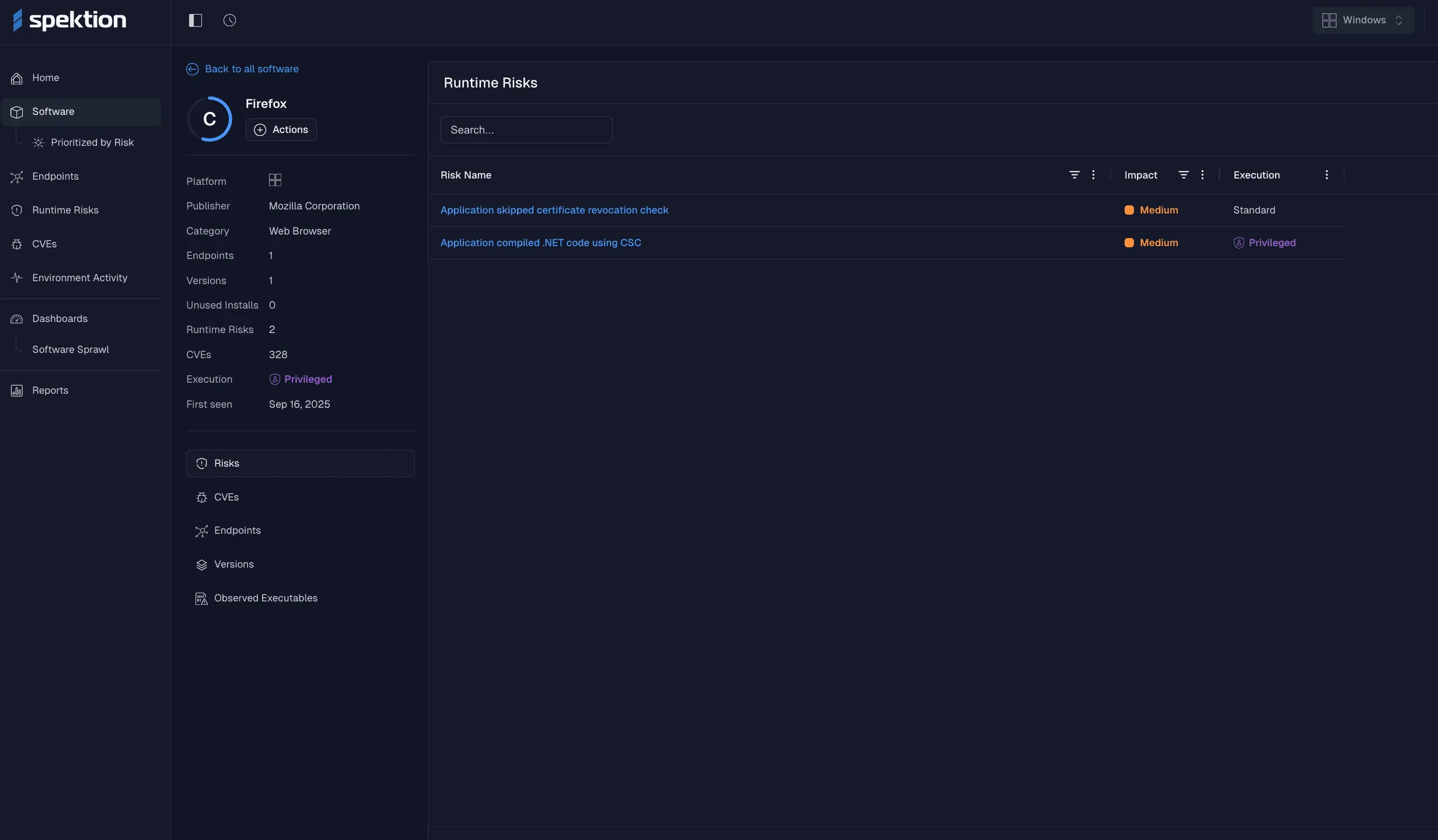
Spektion’s software dashboard, drilled down into a specific piece of software and its associated risks detected in your environment.
Beyond Third-Party: Visibility Across All Software
While third-party software often gets the spotlight, it’s only one piece of the puzzle. Risk can come from anywhere in your environment:
- Internal and homegrown tools. Software built in-house for specific workflows or teams. Even well-meaning engineers can ship code with gaps, especially when security reviews are light or bypassed.
- Legacy applications and admin tools. Older business-critical apps, along with common support tools like file transfer clients, remote access utilities, and archivers, weren’t built for today’s security standards but still run with elevated privileges in many environments.
- AI-generated tooling and scripts. Just-in-time code or scripts created with AI are often deployed quickly without application security and with little visibility into how they behave at runtime. Spektion provides just-in-time vulnerability management for this software as soon as it executes.
Spektion covers them all. By focusing on what actually executes at runtime, rather than just what’s “installed,” you gain visibility into everything that runs within your environment, regardless of its source. That means fewer blind spots, fewer surprises, and more confidence in the tools your teams rely on.
In addition, when risky software behavior is discovered, Spektion makes it actionable, integrating with tools like ServiceNow and Jira so teams can assign, track, and resolve issues in the systems they already use.
For highly regulated industries like finance, healthcare, and energy, software risk is also a major compliance, safety, and resilience requirement.
-
Banks and financial institutions face strict oversight around third-party risk (think DORA in the EU or FFIEC guidance in the US). They need to prove not just that they asked vendors for documentation, but that they understand how software actually behaves in their environment.
-
Healthcare organizations have patient data, life-critical systems, and a regulatory mandate to protect them. A single piece of unvetted software can create outsized liability.
-
Energy companies, along with FSIs and healthcare, face the growing challenge of zero-day vulnerabilities and pre-CVE risk. Attackers aren’t waiting for a CVE to be published, and neither can defenders.
Spektion surfaces risks before CVEs exist and helps teams prioritize which issues are most urgent when a CVE does appear. That means faster, more confident decisions and a defensible posture when regulators (or auditors) come knocking.
This approach also strengthens Continuous Threat Exposure Management (CTEM) programs by extending visibility beyond CVEs to the exposures created by software actually running in your environment.
Confidently Assess Third-Party Software Security
Currently, most organizations evaluate third-party software using a combination of checklists and trust. The best you can hope for is that nothing goes wrong.
With Spektion, hope gets replaced by confidence. You finally see how software behaves at runtime, before or after purchase, and you use that data to decide whether to keep it, restrict it, or push the vendor to reduce the risk.
The result?
- Fewer blind spots in your attack surface.
- Real risks prioritized over theoretical ones.
- Unpatchable vulnerabilities are contained without disruption.
- Governance proven across third-party, internal, and AI-generated software.
It’s a simple but powerful shift: from blind trust to informed control.
Run your next software evaluation with Spektion, or install it on your endpoints and servers to assess software you already use. You’ll finally know what’s really happening under the hood.
Want to see how it works? Book a demo and we’ll show you exactly how to use Spektion to assess your third-party software risk.