Runtime Vulnerability
Management (RVM)
Surface dangerous risks in software without relying on CVEs.
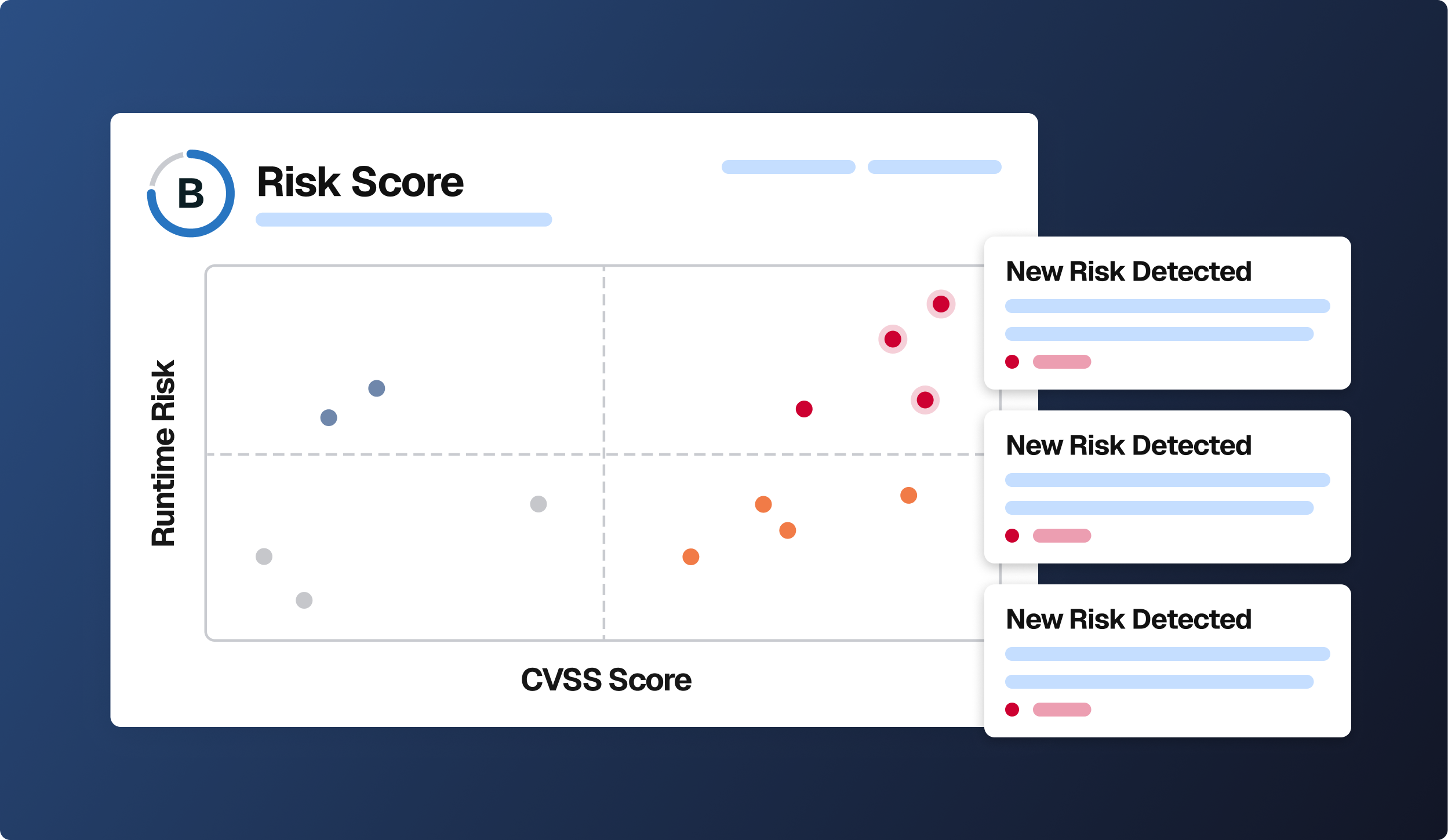
RVM starts vulnerability management at the lowest possible level of observable application behavior, monitoring for risky actions, misconfigurations, and privilege escalations in the runtime environment created when software is in use.
Watch Spektion detect risk in live software
Runtime vulnerability management technology explained
RVM works by monitoring for insecure software behavior in your existing runtime environment. New insecure behavior represents a deviation from an established baseline.
Here's how Spektion's RVM technology helps vulnerability management teams make smart, fast mitigation decisions in complex systems.
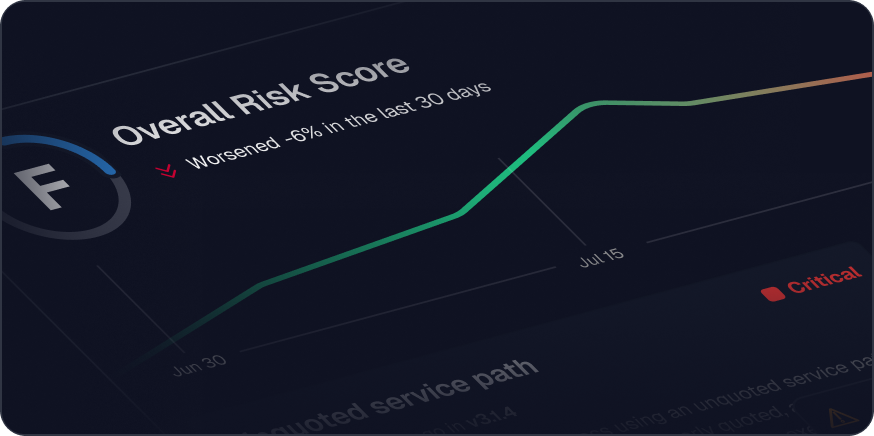

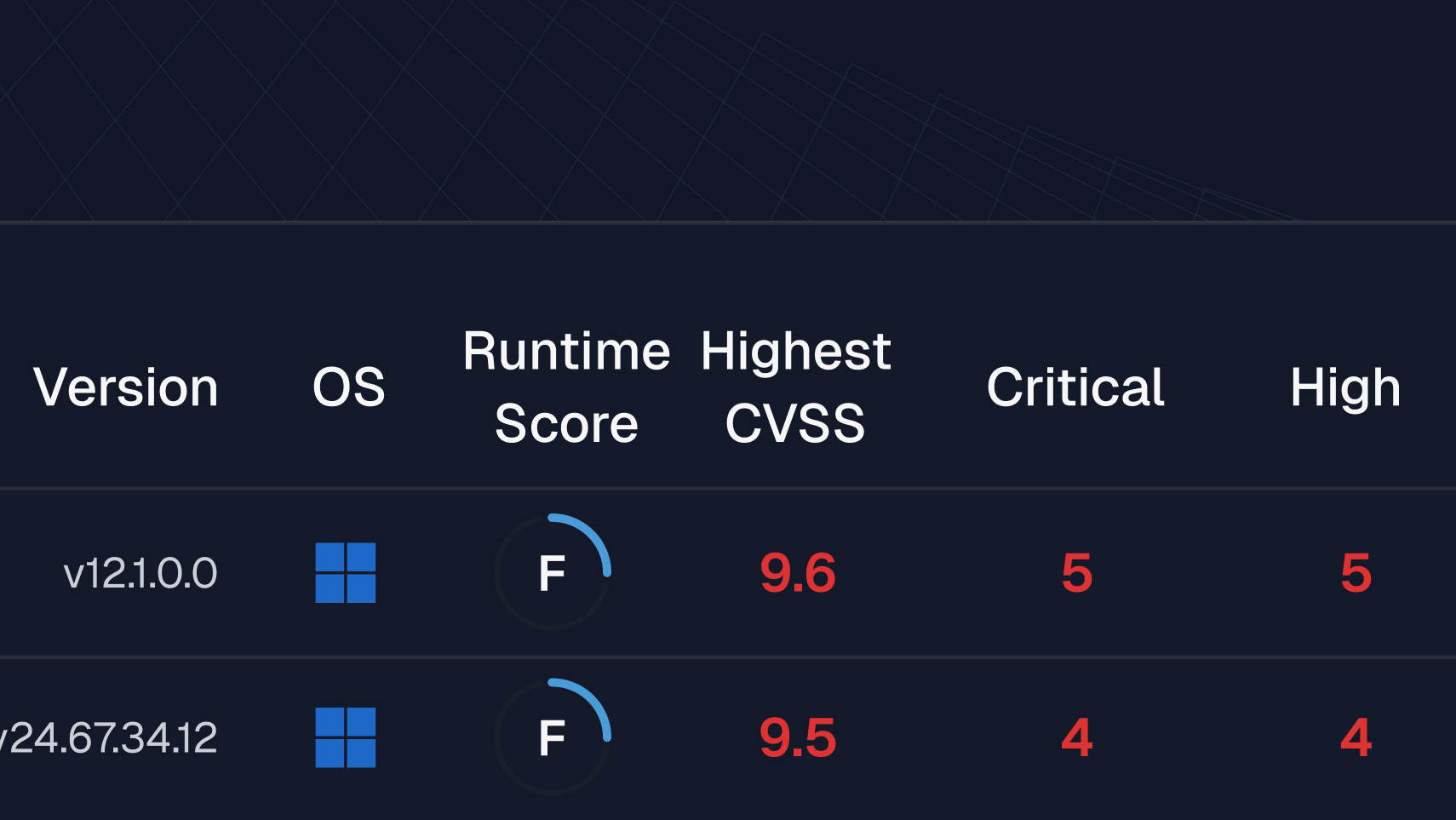
Runtime Vulnerability Management Use Cases
Uncover risks without CVEs or enrich CVSS scores with real-world context to address the full vulnerability risk of everything running.
Bring security into proof-of-concept testing for software to better understand the risk before you procure or deploy broadly.
Identify and mitigate risky software behaviors and abnormal privilege use before a CVE is ever assigned to an exploitable risk.
Automatic, behavior-based risk prioritization without manual investigation. Perfect for small teams with expanding environments who need a risk-based prioritization system to address all their software.
Identify insecure deviations in software behavior to understand the implication of changes or compromise to the software’s supply chain.
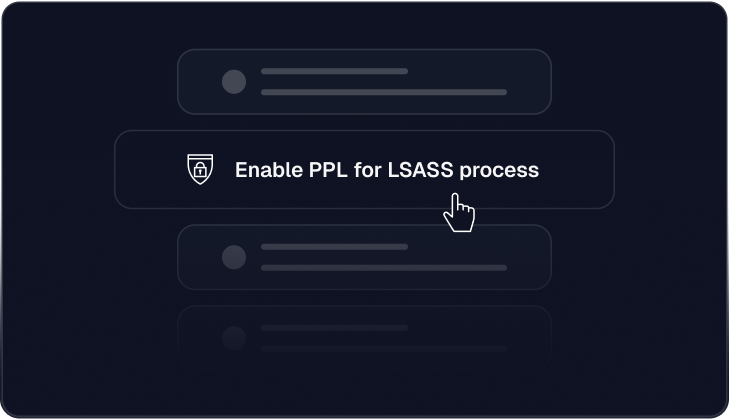
RVM provides compensating controls when a patch is not available or possible.

What’s missing in your VM strategy?
RVM Evolves Vulnerability Management
RVM transforms vulnerability management from a reactive, triage-based process into a proactive, scalable approach. Get ahead of vulnerability risk and build a compelling business case for change.

Focused Risk Intelligence for All Your Software risks
RVM can find risks from all the software applications in your environment, including third-party and open-source software, internal applications, and shadow IT.
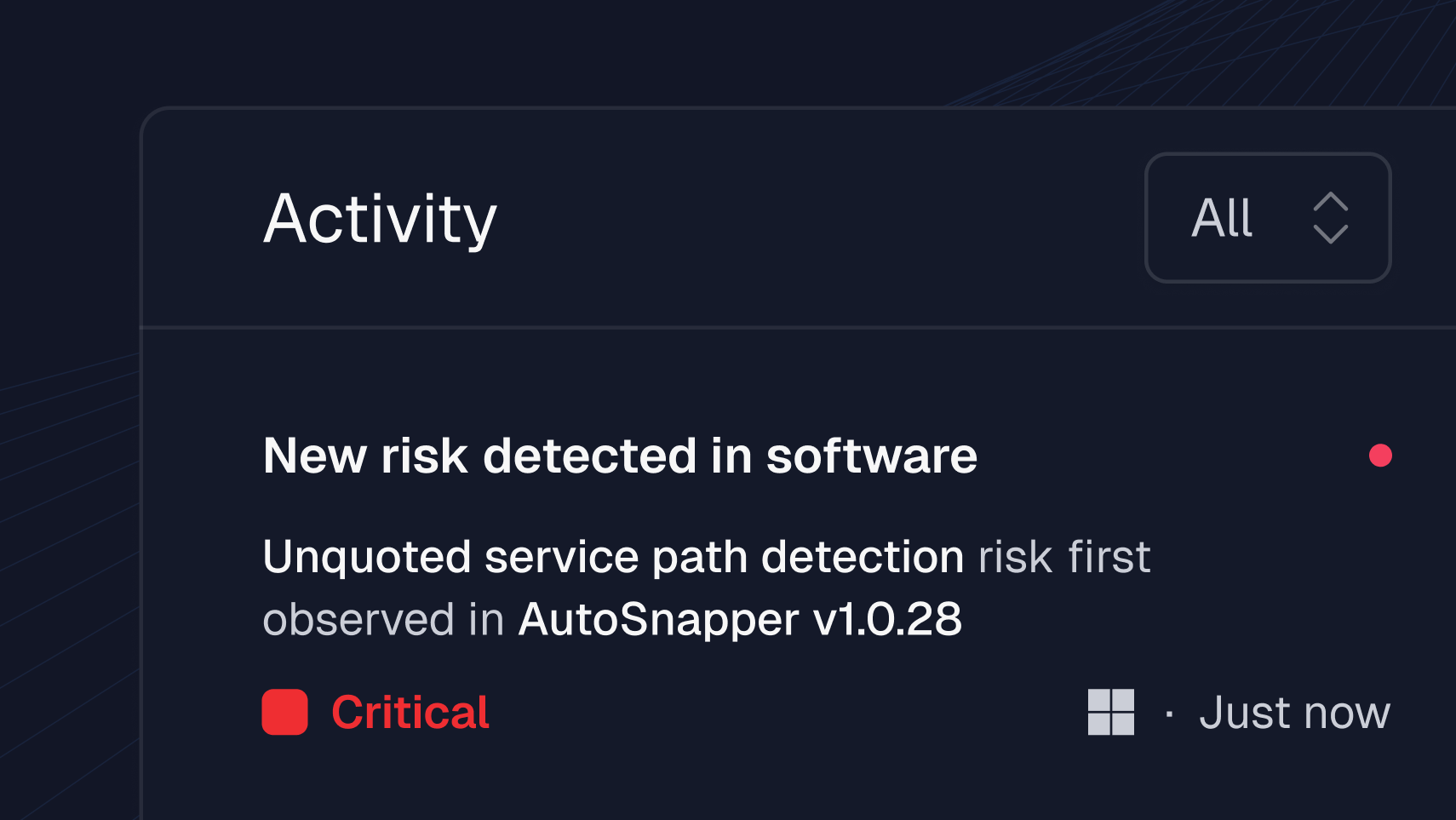
Spotting exploit pathways before they become CVEs, RVM can see risk indicators such as:
- AI-generated code retrieving credentials with broader access rights than necessary .
- A trusted application accessing sensitive memory regions unexpectedly.
- Software establishing insecure network connections.
- Applications requesting elevated privileges beyond their baseline behavior.
- Processes exhibiting characteristics consistent with malware behaviors.
Combining behavioral signals with known data, runtime vulnerability management is how teams make decisions based on what’s actually risky in your environment - not just what’s theoretically vulnerable.
Frequently Asked Questions
RVM is a security approach that detects real-world software risks by observing how applications behave while running, regardless of whether they have known vulnerabilities (CVEs).
Learn more here: What Is Runtime Vulnerability Management
Because runtime is where actual exploitation occurs. RVM shows how software operates in your environment, providing a clearer and more accurate risk picture than theoretical vulnerabilities.
Traditional tools rely on CVEs and static scans. RVM monitors software in real time, flagging risky behavior, misconfigurations, or exploit paths that may not be documented in a CVE database.
RVM can detect risks that CVE-based tools like vulnerability scanners can’t, including:
- Exploitable software behavior with no associated CVEs.
- Shadow IT or “vibe-coded” applications.
- Supply chain and third-party software vulnerabilities.
- Misuse of privileges or insecure runtime configurations.
No. Runtime Vulnerability Management provides a comprehensive view that includes and enriches CVE-based vulnerability management.
RVM incorporates CVE data when available while expanding beyond traditional vulnerability databases to identify behavioral risks, logic flaws, and configuration issues that CVEs don't capture.
This broader perspective helps you prioritize actual risk in your environment. It offers diverse mitigation strategies beyond just patching, including behavioral controls, access restrictions, and runtime protections.
Yes. Spektion is a Runtime Vulnerability Management solution.
Spektion uses a lightweight, passive sensor to:
- Monitor all running software.
- Establish a behavioral baseline.
- Flag insecure patterns in memory, privilege usage, or network access.
- Provide enriched CVE context where applicable.
- Enable proactive Runtime Vulnerability Management.
- RVM vs RASP: RVM captures vulnerability risk across all software, not just web apps. RASP detects potential attack activity against web apps that you host.
- RVM vs EDR: EDR provides real-time visibility into attack activity. RVM complements EDR with real-time visibility into pre-attack exploitability of what is running on your systems.
- RVM vs SAST/DAST/SCA: SAST/DAST/SCA are application security tools designed to introduce security into your SDLC for software you develop. RVM captures vulnerability risk across all software running on your systems—whether you developed it, purchased it, or inherited it—by monitoring real-world runtime behavior and conditions.
- CVE overload: RVM prioritizes real risk, not just severity scores.
- Limited staff: RVM enables small teams to manage more risk with behavioral insights and compensating controls that scale.
- Blind spots: RVM uncovers vulnerabilities in niche or shadow software.
- Ineffective patching: RVM prioritizes remediation efforts where they'll have real impact and addresses the root causes behind multiple CVEs by enabling proactive risk mitigation before vulnerabilities are formally published.
Runtime Vulnerability Management focuses on the behavior of software running in production to identify risk regardless of CVE coverage.
On the other hand, application security focuses on code, configuration, and known issues before or during deployment to prevent vulnerabilities from reaching production.
RVM can assess risks in software you don't own, including third-party applications and supply chain software, while traditional AppSec tools are limited to code you control.