New in Spektion: See Your Unused Software—And Shrink Your Attack Surface
New feature, Unused Software, helps security teams reduce risk, cut costs, and shrink their attack surface.

Published on
At Spektion, we believe one of the most powerful ways to reduce security risk is also the simplest: remove the software you don’t use. Unused software isn’t just a potential entry point for attackers, it’s also a drain on your budget, your team’s time, and your security focus. You’re paying to license it and burning cycles to monitor it—all for something no one is using.
We’re excited to introduce a new capability in Spektion’s runtime vulnerability platform that helps security teams do just that. Our latest feature automatically shows you where software is installed but not actually being used, enabling you to reduce risk, save on licensing, and clean up your environment with confidence.
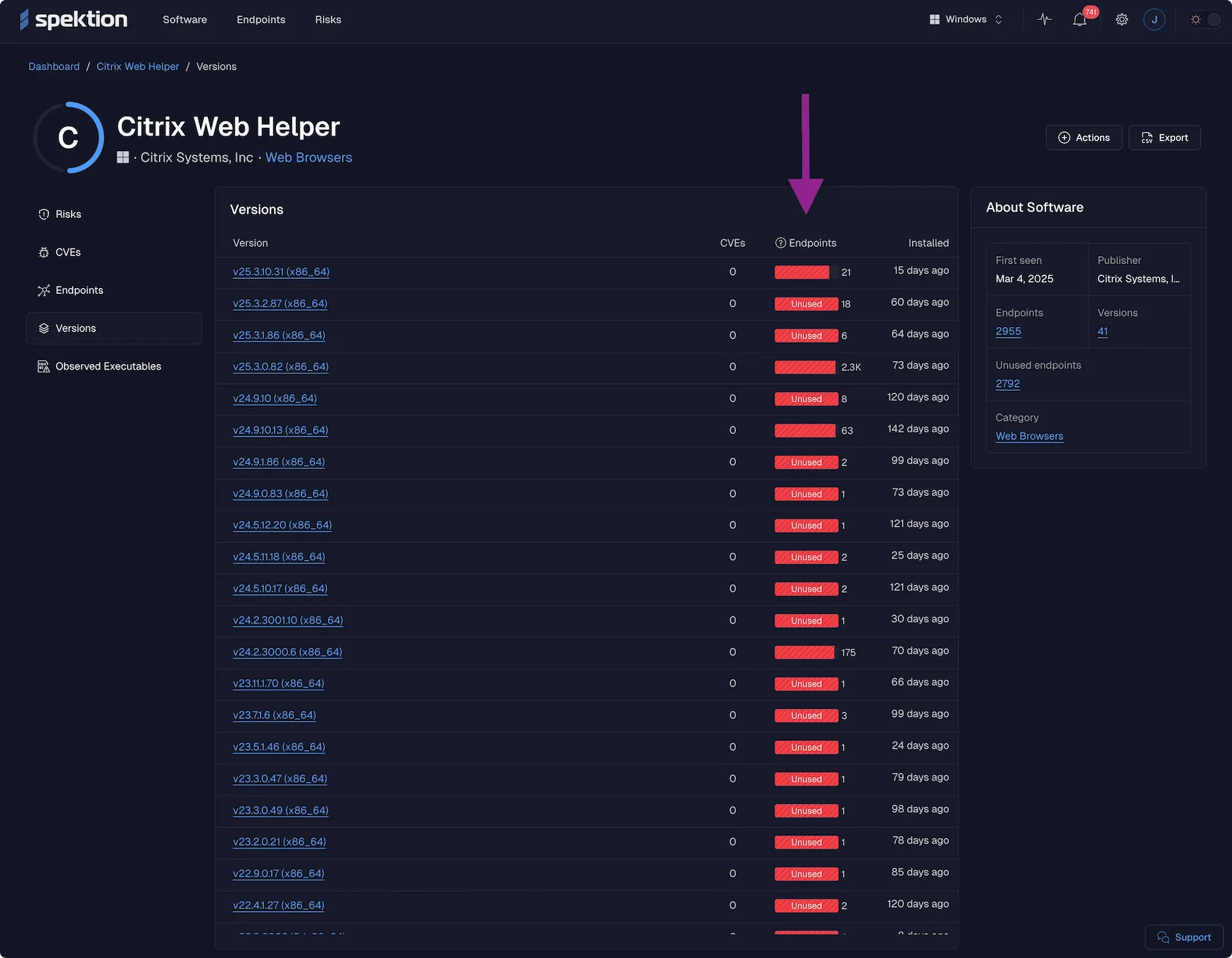
Figure 1: Example of Spektion dashboard showing unused software
What makes Spektion different?
Traditional vulnerability scanners tell you what’s installed. Spektion goes a step further. Because we operate at runtime, we see not just what’s installed, but what’s actually executing. That means we can reliably identify software that is:
- Installed on endpoints
- Not being run or used
- Still posing a risk—just by being present
Why unused software matters
Unused software often flies under the radar. But it still:
- Expands your attack surface
- Increases the potential for privilege escalation
- Creates unnecessary license spend
- Adds complexity to vulnerability management
Now, instead of patching and managing every piece of software in your environment, you can ask a more strategic question: Can we just remove it?
Real-world risk reduction examples
215 hidden tools caught at runtime
One Spektion customer was evaluating a new remote management tool. During the assessment, Spektion flagged that:
- The software was already present in their environment due to a past acquisition
- It was listening on every system, yet didn’t validate certificates
- Worse, it wasn’t even being actively used on the endpoints
That insight allowed the customer to avoid introducing new risk, clean up legacy exposure, and cut licensing waste—all before signing a new vendor contract.
27% less exposure in 30 days
Another Spektion customer reduced their software exposure footprint by 27% in just 30 days by identifying and removing unused software they were previously unaware of.
How it works
With our unused software detection feature, you can:
- Instantly view a list of unused software across your endpoints
- Filter by risk, privilege level, or category (e.g., remote access, dev tools)
- Make informed decisions about what to remove, remediate, or investigate
And because this is Spektion, you also get runtime risk scores and behavioral analysis for each application, so you know not just what is unused, but how risky it really is.
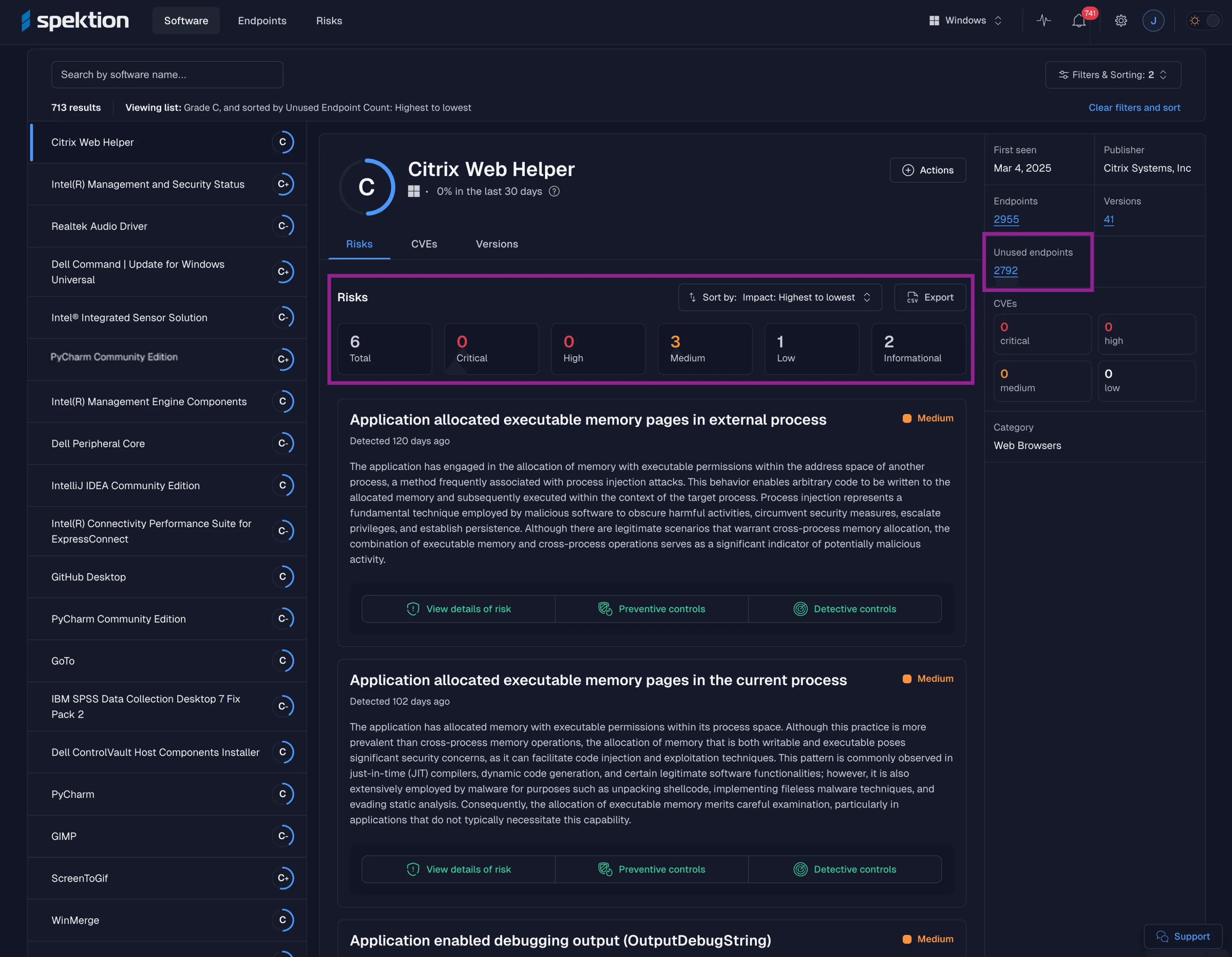
Figure 2: Example of Spektion dashboard showing risks in unused software
Next steps
Ready to shrink your attack surface the easy way? Unused software visibility is now available in the Spektion platform.
✅ Existing customers: Log in and filter by “Unused Software” to explore your environment and take immediate steps to eliminate risk on software no one is using.
💬 Not using Spektion yet? Get in touch for a live demo and see how we can help you wrangle your risk.